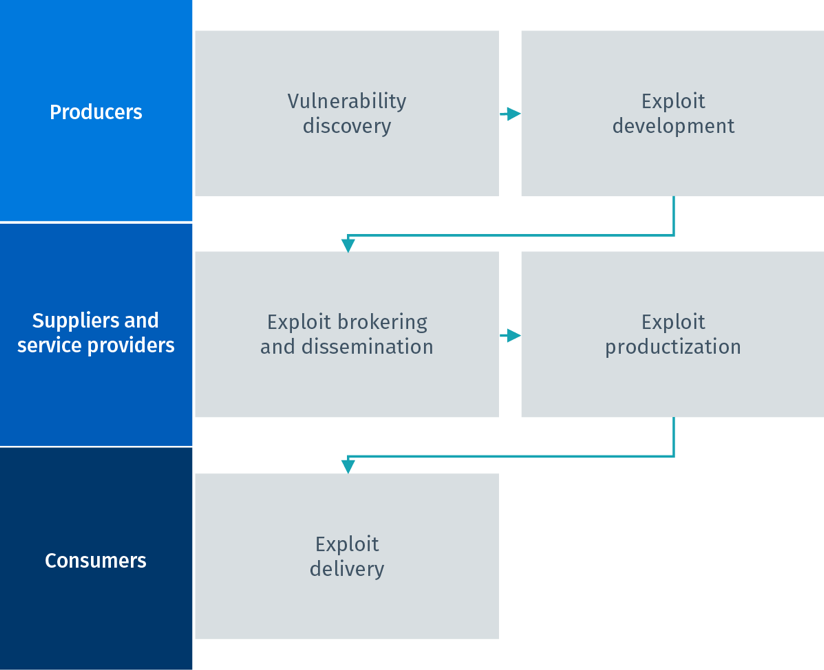
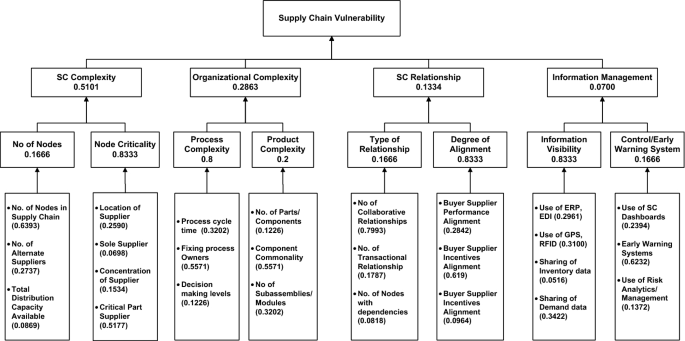
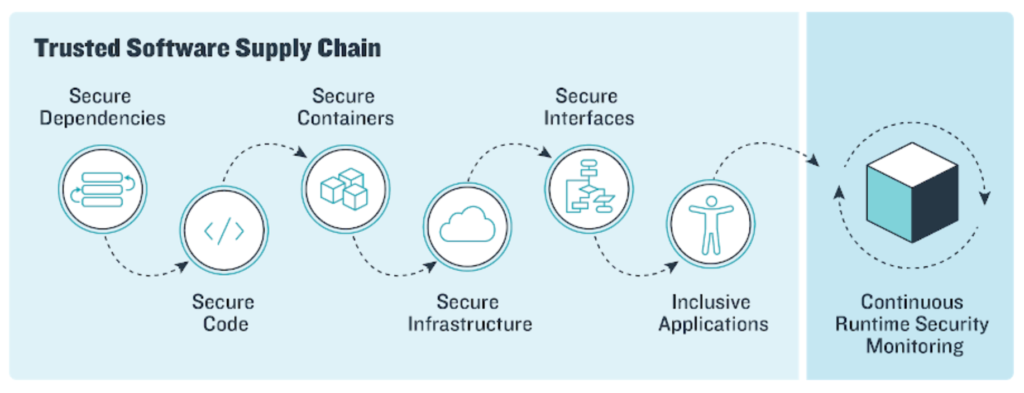
Supply chain vulnerability assessment: A network based visualization and clustering analysis approach - ScienceDirect
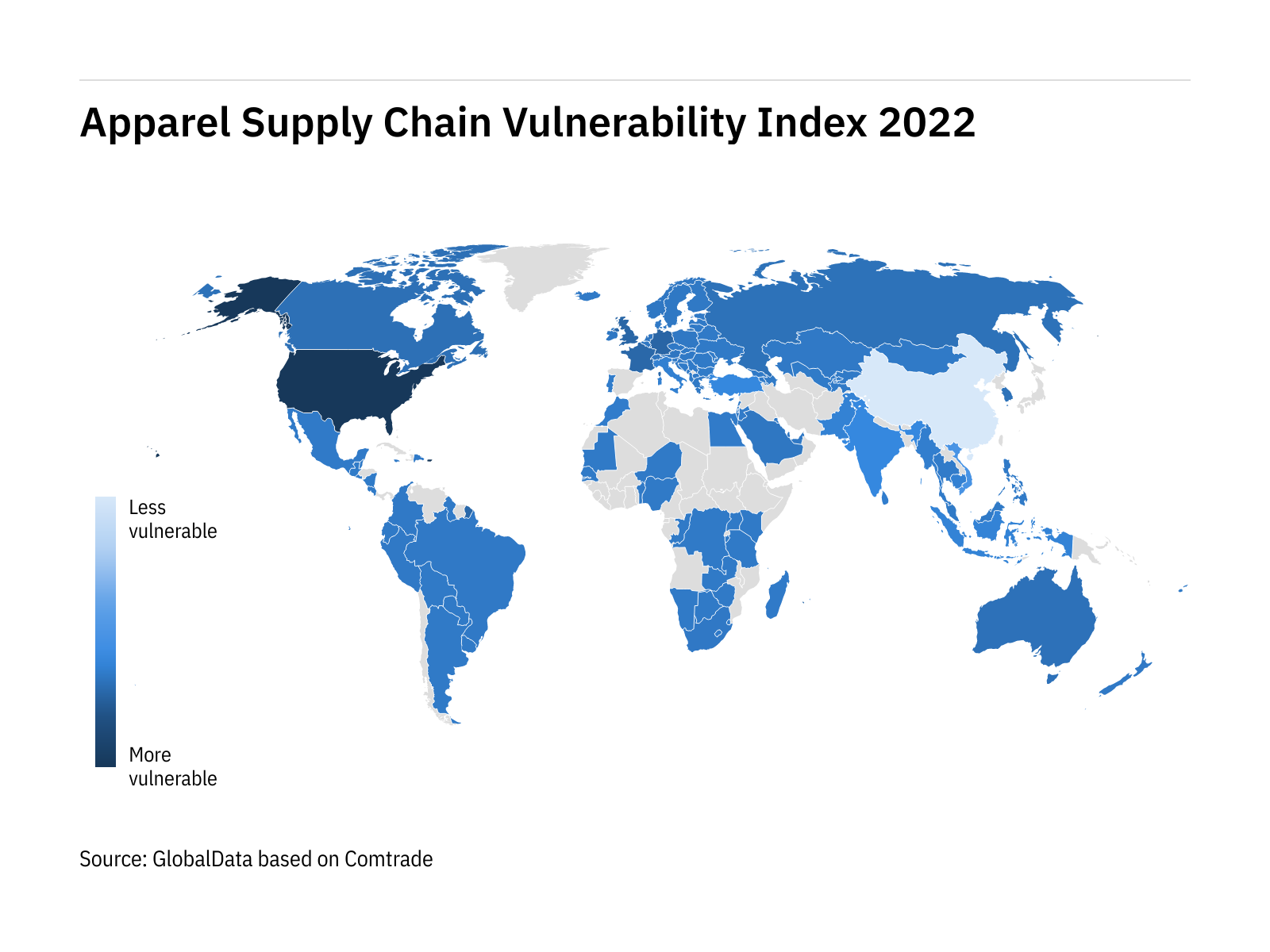
China's resilience shines through in index of world's most vulnerable apparel supply chains - Just Style

Buildings | Free Full-Text | Resilient Capabilities to Tackle Supply Chain Risks: Managing Integration Complexities in Construction Projects

Amazon.com: Supply Chain Risk Management: Vulnerability and Resilience in Logistics: 9780749463939: Waters, Donald

Minimizing the vulnerabilities of supply chain: A new framework for enhancing the resilience | Semantic Scholar

Spectrum of supply chain vulnerabilities: examples of potential disruptions | Download Scientific Diagram

PPT - Supply Chain Vulnerability, Risk, Robustness & Resilience PowerPoint Presentation - ID:9092466

The Supply Chain Vulnerability Scan from Cosmo Tech is now Available on the SAP® Store | Business Wire








![PDF] Assessing the vulnerability of supply chains using graph theory | Semantic Scholar PDF] Assessing the vulnerability of supply chains using graph theory | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c50328abeea3d9dea2146af86d1ca90996de067d/3-Figure2-1.png)